
Decoding Nodes of Digital Security
Digital Security is the practice of protecting digital data, systems, and networks from unauthorized access, breaches, and cyber threats. It encompasses a range of strategies, technologies, and measures aimed at ensuring the confidentiality, integrity, and availability of digital assets. In an increasingly digitized world, where information is stored, processed, and transmitted electronically, robust Digital Security is crucial to safeguard sensitive information, prevent cyberattacks, and maintain trust in digital interactions.Essential Drive
Our Digital Security services are driven by the imperative to fortify organizations against escalating cyber threats. As businesses increasingly rely on digital platforms, the protection of sensitive data, critical systems, and user trust becomes paramount. Our dedication stems from recognizing the multifaceted risks – from operational disruptions to reputational damage – that can arise from breaches. By leveraging advanced technologies and strategies, we safeguards businesses' digital assets, ensures regulatory compliance, and upholds the trust of customers in the rapidly evolving digital landscape.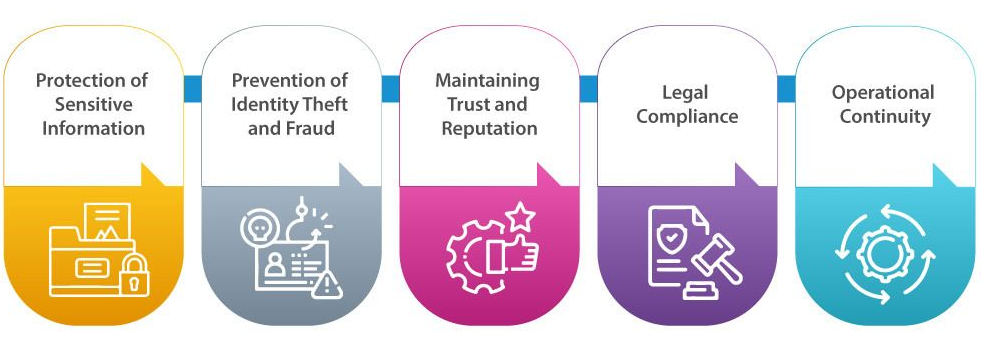

Future Trajectory
Munish IT Solutions envisions a future of Digital Security that's agile and innovative. Leveraging AI, we'll predict and counter emerging threats in real-time. Embracing Zero Trust, we'll ensure continuous verification for robust defense. Quantum-resistant encryption will be our shield against evolving computing threats.
Blockchain's decentralized security will redefine authentication and access control. Automated incident response, driven by machine learning, will swiftly neutralize breaches. Our IoT solutions will protect interconnected ecosystems, and compliance solutions will evolve to match regulations.
Dynamic user education will empower individuals to safeguard digital realms. Munish IT Solutions's future in Digital Security promises adaptability, innovation, and resilience, ensuring a secure digital landscape for businesses to thrive.
Our Digital Security Services offering
1. Strategic Consultation: In-depth analysis and guidance to identify vulnerabilities, devise strategies, and ensure robust digital security.
2. Penetration Testing: Rigorous assessments to uncover system weaknesses, enabling proactive threat mitigation.
3. Vulnerability Management: Continuous monitoring and swift resolution of vulnerabilities to bolster overall security.
4. Security Audits: Thorough evaluations of infrastructure, policies, and practices for compliance and resilience.
5. Identity and Access Management (IAM): Implementation of advanced IAM solutions to control access and ensure authorized usage.
6. Encryption Expertise: Utilization of cutting-edge encryption protocols to safeguard data integrity during transmission and storage.
7. Real-Time Security Monitoring (SIEM): Active surveillance, prompt detection, and immediate response to security events.
8. Intrusion Detection and Prevention (IDPS): Swift identification and prevention of unauthorized access or malicious actions.
DevT's refined Digital Security services offer a holistic approach, combining strategic insights and advanced technologies to fortify businesses against cyber threats, ensuring data protection and user trust.

Advanced Technology for Digital Security
1. AI-Driven Threat Detection: We integrate advanced AI algorithms for real-time anomaly detection, predictive analysis, and behavior recognition, enhancing threat identification and response.
2. Blockchain Security: Utilizing blockchain's decentralized and tamper-proof nature, we ensure secure transactions, robust identity management, and data integrity against unauthorized access.
3. Machine Learning Risk Analysis: We aim to deploy machine learning algorithms to assess vast datasets, identifying potential security risks and enabling proactive risk mitigation strategies.
4. Biometric Authentication: Leveraging biometric technologies like fingerprints, facial recognition, and voice authentication, We provide secure user access controls, minimizing unauthorized entry.
5. IoT Protection: Implementing secure protocols, encryption, and access controls, We safeguard IoT ecosystems, ensuring data and device security in interconnected environments.
6. Cloud Security Expertise: We specialize in securing cloud-based infrastructures, applications, and data. Employing advanced tools, we ensure data confidentiality, integrity, and availability in cloud settings.
Munish IT Solutions's technology offerings for digital security combine AI, blockchain, machine learning, biometrics, and IoT protection to fortify businesses against evolving threats, securing digital assets, and fostering customer trust.